What you need to know about enterprise search security
Enterprise search systems have become the backbone of modern workplace productivity, indexing vast amounts of organizational data to make information instantly discoverable across departments and teams. Yet this powerful capability creates a fundamental tension: how can organizations democratize access to knowledge while protecting their most sensitive information from unauthorized exposure?
The stakes have never been higher for enterprise search security. Knowledge workers now spend up to 20% of their time searching for information across fragmented systems, while data breaches through improperly secured search platforms can expose everything from financial records to intellectual property, potentially triggering regulatory fines and lasting reputational damage.
Today's enterprise search security extends far beyond basic password protection to encompass real-time permission synchronization, advanced encryption protocols, and sophisticated compliance frameworks. Organizations must balance the competing demands of accessibility and protection, ensuring that employees can find what they need to work effectively while maintaining the confidentiality, integrity, and availability of business-critical data.
What Is enterprise search security?
Enterprise search security refers to the comprehensive measures and protocols designed to protect sensitive organizational data while enabling authorized access across multiple systems and platforms. Unlike consumer search engines that index publicly available information, enterprise search must navigate a complex landscape of permissions, data classifications, and regulatory requirements — all while maintaining the speed and accuracy users expect.
At its core, enterprise search security encompasses authentication mechanisms, access controls, data encryption, and compliance frameworks that ensure only the right people can find and view the right information. This goes beyond simple login credentials; modern systems must manage permissions across diverse data sources ranging from on-premises databases to cloud applications, each with its own security model and access requirements. The challenge lies in creating a unified search experience that respects these disparate permission structures without creating security gaps or information silos.
Modern enterprise search security has evolved to address the realities of today's distributed work environment. Real-time permission synchronization ensures that search results always reflect current access rights — when an employee changes roles or leaves the organization, their search access updates immediately across all connected systems. Advanced platforms achieve this through federated architectures that query source systems directly rather than maintaining static copies of sensitive data. This approach, combined with sophisticated encryption for data in transit and at rest, creates multiple layers of protection while preserving the seamless user experience that drives adoption and productivity gains.
Why enterprise search security matters for your organization
The ability to access and analyze data quickly and securely is not just a convenience; it's a strategic imperative. As knowledge workers dedicate substantial portions of their day to locating vital information, the efficiency of enterprise search systems directly impacts organizational productivity and competitive advantage. Inadequately secured search platforms risk data compromises that could inadvertently expose sensitive corporate assets, resulting in financial losses and operational disruptions.
As enterprises integrate more SaaS applications and cloud services, each new connection introduces potential security gaps. Enterprise search systems must serve as both a connective hub and a fortified barrier, protecting against unauthorized intrusions. This centralized access simplifies information retrieval while demanding rigorous protection measures to ensure confidentiality and prevent potential vulnerabilities from being exploited.
The shift to remote work environments underscores the necessity for robust enterprise search security. Employees require seamless access to organizational knowledge without the delays associated with traditional methods. Secure search systems enable this by providing direct, controlled access to data, thus maintaining organizational continuity and enhancing data protection. Compliance with regulations like GDPR, HIPAA, and SOC 2 is essential, as they establish clear guidelines for safeguarding sensitive information, reinforcing the trust necessary for effective data management in an increasingly interconnected world.
Core security components of enterprise search systems
Authentication and access control
Authentication and access control serve as the frontline defenses of enterprise search systems, ensuring only authorized users can access sensitive information. Role-based access control (RBAC) assigns permissions based on specific job functions, departments, and data sensitivity levels, creating a layered security framework. This allows organizations to define access parameters that align with their operational needs, effectively minimizing the risk of unauthorized data exposure.
Multi-factor authentication (MFA) further enhances security by requiring additional verification beyond passwords, significantly reducing the potential for credential theft. Single sign-on (SSO) integration with identity providers such as Active Directory, Okta, or Azure AD streamlines user access across multiple applications while maintaining robust security standards. OAuth 2.0 protocols facilitate secure authorization, allowing users to access resources without exposing their credentials to the search system, thereby safeguarding against potential vulnerabilities.
Data encryption protocols
In the realm of enterprise search systems, data encryption stands as a critical safeguard for maintaining data integrity and confidentiality. Employing robust encryption protocols like AES-256 ensures that data stored within search indexes remains protected from unauthorized access, even in the event of a system breach. This high standard of encryption provides a formidable defense, preserving the confidentiality of sensitive information.
To protect data in transit, implementing secure protocols such as TLS 1.3 is essential. It guarantees that communications between users, the search platform, and interconnected data sources are shielded from interception and eavesdropping. By utilizing comprehensive encryption measures throughout the search and retrieval process, organizations can deter unauthorized access at every juncture. Additionally, sophisticated encryption key management practices, such as regular key rotation and separate storage, further enhance security by reducing the risk of key compromise.
Dynamic permission adjustments
Dynamic permission adjustments are vital for safeguarding access controls in adaptable enterprise environments. By instantly updating permissions to reflect changes in source systems, organizations close off potential security loopholes associated with outdated access rights. This adaptable approach ensures that search results dynamically align with the current permissions of each user, automatically concealing restricted content from unauthorized eyes.
Cross-platform permission harmonization supports a cohesive security framework across a variety of data sources and systems, adapting seamlessly to an organization's changing demands. Comprehensive audit trails meticulously document permission changes and access attempts, providing invaluable insights for security monitoring and compliance verification. This approach not only fortifies data security but also aids in meeting regulatory requirements, underscoring the organization's dedication to protecting sensitive information.
How modern enterprise search handles sensitive data
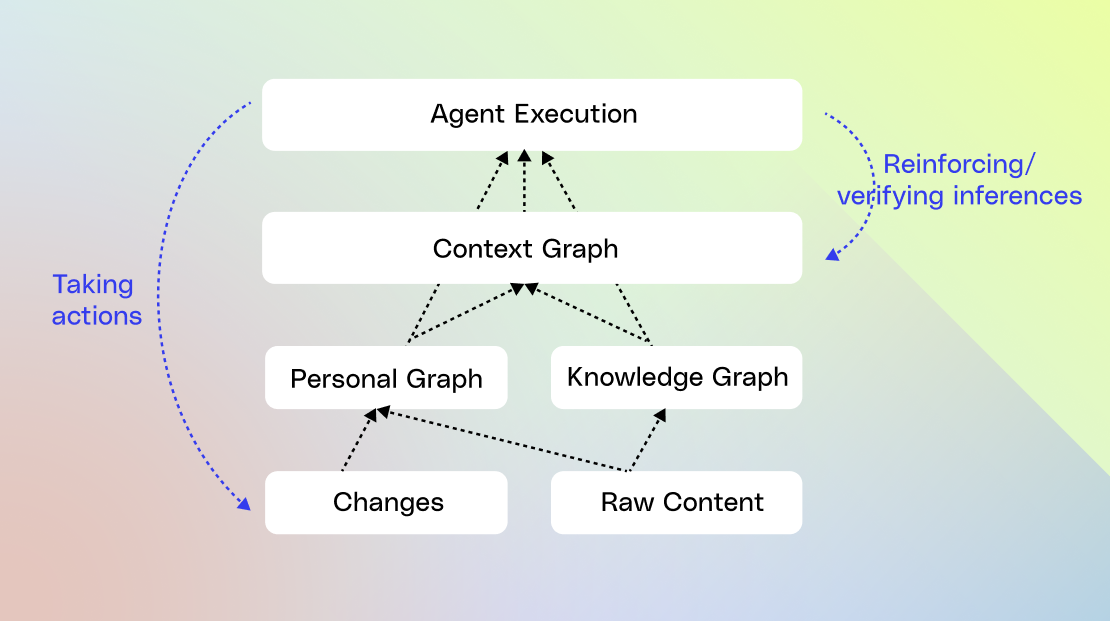
Navigating the complexities of data protection within enterprise search systems requires innovative solutions that prioritize both security and seamless access. Advanced architectures utilize real-time data querying without retaining sensitive information in centralized indexes. This approach reduces potential vulnerabilities by keeping sensitive data within its original repositories, accessed only when necessary for specific queries.
Modern systems emphasize ephemeral data handling, ensuring that search queries and their results are transient, existing only during active sessions. This minimizes exposure risks by avoiding long-term data retention, aligning with best practices for reducing unauthorized access opportunities. By limiting data persistence, enterprises can significantly decrease the chances of breaches that compromise sensitive information.
A critical component of these systems includes sophisticated data filtering techniques, which actively identify and mitigate exposure of confidential patterns like financial details or personal identifiers. This ensures that search outputs are sanitized before reaching end-users. Furthermore, dynamic security measures apply varying levels of protection based on data sensitivity, user roles, and device integrity. This adaptive framework guarantees that only authorized personnel access highly sensitive information, tailored to their specific context.
By adopting a model that continuously evaluates and validates user access requests, these systems eliminate assumptions of trust based on user location or previous authentications. This ongoing verification process ensures robust security, even within internal networks. Additionally, protective measures like automatic data masking and redaction shield sensitive fields from unauthorized views, ensuring that search previews only reveal information to those with appropriate access rights. Through these comprehensive strategies, enterprise search systems maintain optimal security while delivering the accessibility needed for efficient data utilization.
Compliance and regulatory requirements
Adhering to compliance and regulatory standards within enterprise search systems is essential for maintaining data security and user privacy. Organizations must implement robust information security frameworks to mitigate risks and meet regulatory requirements. Certifications like ISO 27001 provide a comprehensive structure for managing information security, encompassing policies and procedures that protect data assets. Additionally, ISO 27701 focuses on privacy, detailing guidelines for handling personal data in accordance with international privacy laws, thereby reinforcing a proactive approach to data protection.
SOC 2 Type II attestation offers a rigorous evaluation of a company's security practices over a defined period, ensuring adherence to high standards. To maintain a proactive stance, organizations benefit from regular external security assessments that provide insights into potential vulnerabilities and verify compliance with evolving standards. Such audits are crucial for enhancing security postures and identifying areas needing improvement, thus ensuring continuous vigilance against emerging threats.
Privacy regulations
Organizations must navigate a diverse regulatory landscape to ensure compliance with privacy laws. The General Data Protection Regulation (GDPR) remains a pivotal framework, requiring organizations to implement measures for data protection and user rights management for EU residents. GDPR compliance reflects an organization's dedication to maintaining high privacy standards and respecting individual data rights.
In the United States, the California Consumer Privacy Act (CCPA) mandates transparency in data handling, including requirements for data access, deletion requests, and opt-out provisions for California residents. In healthcare, the Health Insurance Portability and Accountability Act (HIPAA) provides a framework for protecting patient information through stringent security protocols. Additionally, sector-specific regulations like PCI-DSS for payment data and FERPA for educational records demand tailored security strategies, ensuring sensitive data remains protected within these specialized domains.
Cross-border data considerations
The global nature of data exchange requires careful attention to cross-border data regulations. Data residency requirements often dictate that sensitive information must remain within specified jurisdictions to comply with local laws. This necessitates strategic data management that respects geographic boundaries while facilitating operational efficiency.
To support lawful international data transfers, organizations frequently employ mechanisms such as Standard Contractual Clauses, which provide a legal framework for maintaining data privacy across borders. Additionally, implementing strong data protection measures, including advanced encryption and anonymization techniques, ensures that data remains secure and compliant regardless of its location. These strategies not only protect data integrity but also enable organizations to leverage global data resources while respecting sovereignty and privacy obligations.
Security best practices for enterprise search implementation
Implementing security best practices in enterprise search systems begins with a robust deployment architecture. Single-tenant deployments offer a tailored approach, providing dedicated infrastructure that avoids the complexities and risks associated with multi-tenant environments. This isolation helps prevent data bleed and ensures that resources are not shared among different entities, reducing the potential for unauthorized access. Additionally, network segmentation plays a critical role in enhancing security. By compartmentalizing search systems from other infrastructure components through firewalls and VLANs, organizations can create a more controlled and secure environment.
To safeguard communication channels, securing API interactions is essential. Implementing strong authentication protocols, utilizing token-based access, and encrypting data exchanges between systems help maintain the integrity and confidentiality of information. Regular updates and security patches fortify these systems against emerging vulnerabilities, ensuring that each component remains resilient against potential threats.
Monitoring and incident response
A comprehensive approach to monitoring and incident response is crucial in identifying and addressing potential security threats within enterprise search systems. Advanced monitoring tools provide continuous oversight, detecting deviations from expected search patterns that could signify unauthorized activities. Such proactive measures allow organizations to respond swiftly to potential breaches, minimizing the impact of malicious actions. By integrating search data with broader security intelligence platforms, organizations can achieve a panoramic view of their security posture, enabling more effective threat identification and response.
Automated alert systems are instrumental in incident response, delivering real-time notifications to security teams about activities that deviate from the norm, such as unusual data access or shifts in user permissions. These timely alerts facilitate rapid intervention, curbing the potential for damage. To effectively manage such incidents, organizations should develop and maintain detailed response protocols, outlining specific actions to take when addressing detected threats, thereby ensuring preparedness for a wide range of security scenarios.
User behavior analytics
Leveraging user behavior analytics enhances the security framework of enterprise search systems by providing insights into how users interact with data. Machine learning algorithms can discern normal patterns from anomalies, identifying behaviors that could indicate potential insider threats. This analysis enables organizations to proactively address risks before they materialize into security incidents. By assigning risk profiles to users based on their access patterns and the sensitivity of the data they handle, organizations can tailor security measures to the specific needs of each user.
Dynamic authentication mechanisms further bolster security by adapting verification requirements based on the risk level of access requests. This context-aware approach ensures that sensitive data remains accessible only to those who have verified their identity through multiple factors. Moreover, effective session management practices, such as terminating inactive sessions and requiring re-authentication after prolonged use, contribute to a secure environment, balancing accessibility with protection.
Common security vulnerabilities and how to address them
Tackling common security vulnerabilities in enterprise search systems is essential for preserving a secure environment. One significant threat is SQL injection, where attackers exploit unsanitized input fields to execute harmful code. Mitigation involves utilizing prepared statements and rigorous input validation techniques. With these measures in place, organizations can effectively block this exploit path and protect their databases from unauthorized intrusions.
Cross-site scripting (XSS) remains a frequent threat in web applications, allowing malicious scripts to compromise user data. To mitigate these risks, organizations should implement robust content security policies and employ output encoding methods. These strategies help ensure that unauthorized scripts cannot execute within the search interface, safeguarding the integrity of user interactions.
Addressing privilege escalation vulnerabilities involves ensuring that users do not acquire elevated permissions beyond their roles due to configuration oversights. Implementing the principle of least privilege is crucial, ensuring users have only the access necessary for their duties. Regular audits of access rights further strengthen this approach, keeping permissions aligned with organizational security standards.
API vulnerabilities present critical entry points for potential attacks. Securing these pathways requires enforcing strong authentication protocols and monitoring usage patterns with rate limiting. Comprehensive logging provides insights into access activities, enabling swift detection and response to anomalies, thereby reducing unauthorized data access risks.
Insider threats, often unpredictable, demand a multifaceted response. Alongside technical controls like access monitoring, organizations must prioritize security awareness training. By educating employees about potential risks and fostering a security-conscious culture, the likelihood of insider incidents decreases. Behavioral monitoring tools add an extra layer of detection, identifying deviations from standard user activity.
Risks associated with shadow IT arise when employees use unapproved tools without IT oversight. Network monitoring solutions can detect such unauthorized applications, allowing organizations to enforce usage policies. Actively managing the software environment ensures all tools comply with security protocols, preventing data leaks and maintaining system integrity.
Third-party integration risks highlight the importance of thorough vetting for external connectors and APIs. Before deployment, organizations must ensure these components meet security standards and do not introduce vulnerabilities. This diligence guarantees that third-party integrations enhance system functionality without compromising security.
Building a secure enterprise search strategy
Developing a comprehensive enterprise search strategy requires a robust security assessment framework. Begin with an in-depth evaluation to identify and assess the types of sensitive data within your organization and their potential exposure points. By closely analyzing data flows between systems, you can gain insights into how information traverses your search infrastructure, spotlighting potential vulnerabilities. It's crucial to outline security requirements tailored to your data classifications, regulatory obligations, and organizational priorities. Establishing precise security metrics and KPIs enables continuous monitoring of protection measures to ensure they align with industry benchmarks and organizational objectives.
Implementation roadmap
An effective implementation roadmap initiates with a controlled proof of concept. This step is critical for verifying the functionality and adequacy of your security controls before widespread deployment. Implementing phased rollouts based on specific departmental needs and data sensitivity levels allows for managed risk mitigation. Continuous security testing, including thorough penetration testing and vulnerability assessments, is essential for identifying and addressing new threats. Comprehensive security documentation—encompassing policies, procedures, and user instructions—lays the groundwork for maintaining high security standards across the organization.
Ongoing security management
Sustaining ongoing security management is vital for adapting to the dynamic threat landscape. Regularly scheduled security reviews are crucial for evaluating the performance and adequacy of your existing controls, ensuring they remain effective and adaptive to new challenges. Security awareness training empowers employees with the knowledge and skills necessary to safeguard enterprise information proactively. Effective vendor management programs are integral, ensuring that external partners adhere to stringent security standards. Business continuity planning is a cornerstone of this strategy, guaranteeing the resilience and availability of search systems during potential disruptions while maintaining data security and integrity.
Enterprise search security isn't just about protecting data — it's about enabling your teams to work confidently and efficiently in an increasingly complex digital landscape. By implementing the security measures and best practices outlined above, you can build a search infrastructure that balances accessibility with protection, ensuring your organization's knowledge remains both discoverable and secure.
Ready to see how modern enterprise search can transform your workplace while maintaining the highest security standards? Request a demo to explore how we can help you build a secure, AI-powered search experience that empowers your teams while protecting your most sensitive information.